1+ Million WordPress sites affected by vulnerabilities that could lead to remote code execution attacks
The Essential Addons for Elementor WordPress plugin, with over a million users recently patched multiple vulnerabilities that could have allowed malicious attackers to run arbitrary code on a targeted WordPress website.
LFI to RCE Attack Vulnerability
According to the U.S. Government NIST website, vulnerabilities on the Essential Addons for Elementor plugin made it possible for an attacker to launch a a Local File Inclusion attack, which is an exploit that allows an attacker to cause a WordPress installation to reveal sensitive information and read arbitrary files.
From there the attack could lead to a more serious attack called a Remote Code Execution (RCE). Remote Code Execution is a highly serious form of attack in which a hacker is able to run arbitrary code on a WordPress site and cause a range of damage, including a full site takeover.
As an example, a Local File Inclusion attack can be accomplished by changing the URL parameters to something that could reveal sensitive information.
This was made possible because the Essential Addons for Elementor WordPress plugin did not properly validate and sanitize data.
Data Sanitization is a process for limiting the kind of information that is possible to be input. In simple terms, data sanitization can be thought of as a lock that allows only a specific input, a key with a specific pattern. A failure to perform data sanitization could be analogous to a lock that allows any key to open it.
According to the United States Government National Vulnerability Database:
“The Essential Addons for Elementor WordPress plugin before 5.0.5 does not validate and sanitise some template data before it them in include statements, which could allow unauthenticated attackers to perform Local File Inclusion attack and read arbitrary files on the server, this could also lead to RCE via user uploaded files or other LFI to RCE techniques.”
Security site WPScan who were the ones to discover first discover and report the vulnerability published the following description:
“The plugin does not validate and sanitise some template data before it them in include statements, which could allow unauthenticated attackers to perform Local File Inclusion attack and read arbitrary files on the server, this could also lead to RCE via user uploaded files or other LFI to RCE techniques.”
Essential Addons for Elementor Patched
The vulnerability was announced on the National Vulnerability Database site on February 1, 2022.
But the “Lite” version Essential Addons for Elementor plugin has been patching vulnerabilities since the end of January, according to the Essential Addons Lite changelog.
A changelog is a software log of all changes made for each version that is updated. It is a record of everything that was changed.
Curiously, the changelog for the Pro version does only mentions “Few minor bug fixes and improvements” but makes zero mention of the security fixes.
Screenshot of Essential Addons For Elementor Pro Changelog
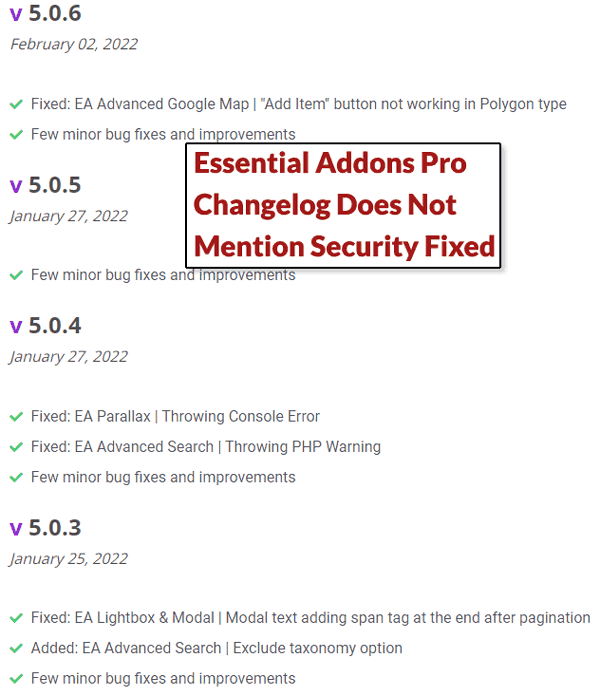
Why is the security fix information missing from the Pro version of the WordPress plugin?
Click here to view original web page at WordPress Vulnerability in Essential Addons for Elementor


![What is Context Marketing? Why It Matters in 2022 [+Examples]](https://b2346413.smushcdn.com/2346413/wp-content/uploads/2022/03/context-marketing-300x200.jpeg?lossy=1&strip=1&webp=1)




